OWASP Top 10 2025 – What’s New and How It Impacts Application Security

Organizational project OWASP (Open Web Application Security Project) has for many years published the Top 10 list of the most critical web application security risks. It serves as a key reference point for developers, auditors, DevSecOps operations, and IT departments. The version OWASP Top 10 2021 has been widely adopted and is becoming a foundation for coding, testing, deployment, and monitoring security standards.
Due to the rapidly changing threat landscape (microservices, API-first, cloud, CI/CD, DevSecOps model, and elements of generative artificial intelligence), OWASP is preparing a new release of the list for 2025 (currently in the Release Candidate phase).
Below we present:
- the key changes and main topics from OWASP Top 10 2021,
- the draft OWASP Top 10 2025 (RC) list – what changes and why,
- a comparison of both lists, along with recommendations for development, security, and IT operations teams.
Table of Contents
ToggleOWASP Top 10 2021 – recap
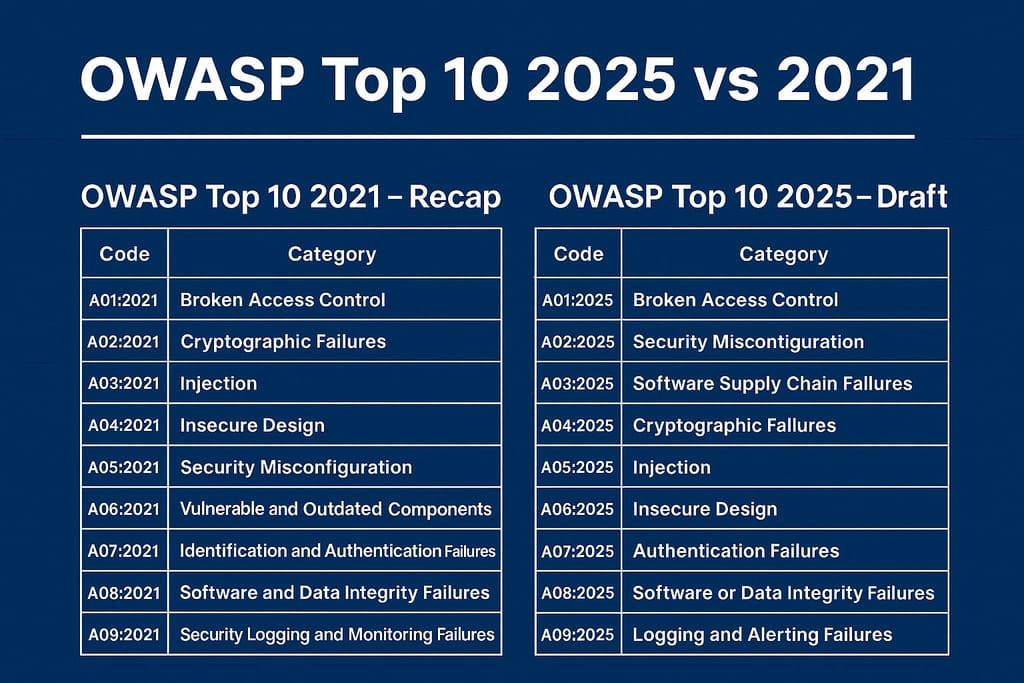
The table below shows the 10 categories from the 2021 version:
| Code | Category | Short explanation |
|---|---|---|
| A01:2021 | Broken Access Control | Violation of access control mechanisms – users perform actions or gain access they are not authorized for. |
| A02:2021 | Cryptographic Failures | Errors in cryptographic implementation (weak algorithms, bad keys, lack of data protection in transit/at rest) – formerly “Sensitive Data Exposure.” |
| A03:2021 | Injection | Injection of code/commands (SQL, OS, LDAP, XSS, etc.). In the 2021 version, XSS was included in this category. |
| A04:2021 | Insecure Design | New in 2021 – focuses on design-level issues, threat modeling, and secure architecture patterns. |
| A05:2021 | Security Misconfiguration | Configuration errors such as default passwords, open ports, or improper server/application settings. |
| A06:2021 | Vulnerable and Outdated Components | Use of components/libraries/frameworks with known vulnerabilities or lacking vendor support. |
| A07:2021 | Identification and Authentication Failures | Flaws in authentication and identification – weak passwords, lack of MFA, improper session handling. |
| A08:2021 | Software and Data Integrity Failures | Integrity violations of data/applications – e.g., unverified updates, missing code validation in CI/CD. |
| A09:2021 | Security Logging and Monitoring Failures | Lack of or improper logging and monitoring, making incident detection and response difficult. |
| A10:2021 | Server-Side Request Forgery (SSRF) | The application performs HTTP/HTTPS requests on behalf of a user without proper validation, allowing access to internal resources. |
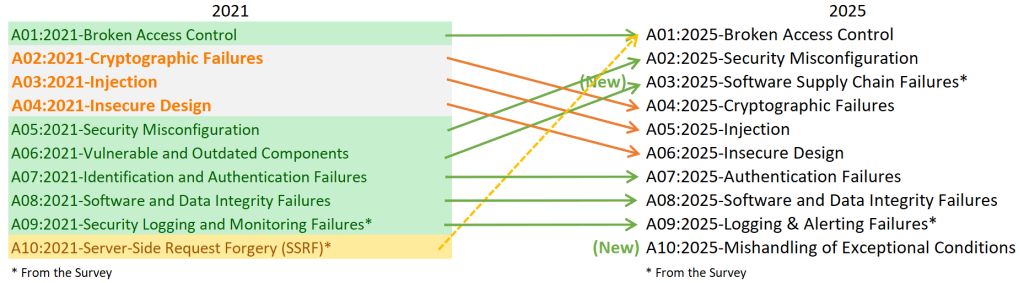
Key changes compared to previous editions:
- “Broken Access Control” jumped to position #1.
- “Insecure Design” and “Software and Data Integrity Failures” were added as new categories.
- Renaming: e.g., “Cryptographic Failures” replaced “Sensitive Data Exposure.”
- XSS merged into the “Injection” category.
For DevSecOps teams, the 2021 list remains a foundational reference (secure coding guidelines, pentesting, audits) – but it is already time to prepare for the upcoming changes.
OWASP Top 10 2025 – draft version (Release Candidate)
Although the final OWASP Top 10 2025 version has not yet been officially released (as of September/October 2025), the project’s site presents the following draft list (RC):
| Code | Category |
|---|---|
| A01:2025 | Broken Access Control |
| A02:2025 | Security Misconfiguration |
| A03:2025 | Software Supply Chain Failures |
| A04:2025 | Cryptographic Failures |
| A05:2025 | Injection |
| A06:2025 | Insecure Design |
| A07:2025 | Authentication Failures |
| A08:2025 | Software or Data Integrity Failures |
| A09:2025 | Logging and Alerting Failures |
| A10:2025 | Mishandling of Exceptional Conditions |
(Source: OWASP Top Ten 2025 RC1)
Explanation and implications of each category
- Broken Access Control (A01) – remains at the top; in 2025, more focus on complex environments: microservices, cloud, federated identities, zero-trust.
- Security Misconfiguration (A02) – moved higher, showing that misconfigurations remain frequent and dangerous in modern architectures.
- Software Supply Chain Failures (A03) – new or heavily redefined; highlights the risks of third-party dependencies, packages, containers, and CI/CD pipelines.
- Cryptographic Failures (A04) – still critical, though slightly lower than 2021; improvements in libraries help, but requirements tighten (e.g., TLS 1.3, AEAD, post-quantum readiness).
- Injection (A05) – remains relevant but expanded to include new attack vectors (GraphQL, APIs, AI models).
- Insecure Design (A06) – still important, though lower-ranked; emphasizes “shift-left” security in software development.
- Authentication Failures (A07) – renamed and refined from 2021; focuses on sessions, tokens, identity federation, and phishing impersonation.
- Software or Data Integrity Failures (A08) – stresses code integration, delivery continuity, and tamper-proof deployment in DevOps pipelines.
- Logging and Alerting Failures (A09) – expanded from the 2021 “Logging and Monitoring” category, now emphasizing real-time alerts, automation, and telemetry.
- Mishandling of Exceptional Conditions (A10) – new or rebranded; covers improper error and exception handling, recovery session logic, and lack of fallback mechanisms.
Comparison of both lists (2021 vs 2025)
Below are key differences and implications:
| Aspect | What changed | Why it matters in practice |
|---|---|---|
| Priority/Position | In 2021, “Broken Access Control” was #1; in 2025, it remains #1 – showing persistent risk. | Teams should continue to prioritize authorization, now considering cloud and API-driven architectures. |
| Category changes | New “Software Supply Chain Failures” (#3 in 2025), absent in 2021. | Teams must focus on dependency management (libraries, containers, CI/CD pipelines). |
| Renaming and scope | “Authentication Failures” replaces “Identification and Authentication Failures”; “Logging and Alerting” replaces “Logging and Monitoring.” | Reflects differentiation between monitoring and real-time alerting processes. |
| New vectors | “Mishandling of Exceptional Conditions” highlights edge-case and microservice/AI-related exception management issues. | Requires architectural review of fallback and exception-handling logic. |
| “Shift-left” and design | “Insecure Design” remains, but lower-ranked – now considered a standard expectation. | Integrate security earlier in design rather than just testing stages. |
| Configuration & operations | “Security Misconfiguration” moves higher – operational configuration remains a major weak point. | Should be part of continuous monitoring and production audits (including CI/CD). |
Recommendations for security/development teams
Based on the above analysis, we suggest that IT/development teams adopt the following actions:
- Update checklists and coding standards
- Prioritize “Broken Access Control”: RBAC/ABAC models, permission mapping, least privilege testing.
- Add “Software Supply Chain Failures”: dependency management (SCA), container scans, CI/CD pipeline security, artifact signing.
- Include exception and boundary condition reviews (“Mishandling of Exceptional Conditions”).
- Expand integration and failure scenario testing (e.g., DB outages, expired tokens, missing resources, container script crashes).
- Training and awareness
- Train developers and architects in areas such as secure design, supply chain security, and production configuration management.
- Update onboarding materials to cover “Authentication Failures” – identity federation, cookie vs token sessions, token abuse.
- Audit / Test / Monitoring processes
- Include configuration, CI/CD, and error monitoring controls in audit and testing plans.
- Define metrics: known vulnerable dependencies, privilege escalation incidents, misconfiguration issues, unhandled production exceptions.
- Adopt automation: SCA scanners, IaC validation (Terraform/Azure Bicep/CloudFormation) with security rules, exception telemetry monitoring.
- Integration with HEXSSL services
- In context of our services (SSL/TLS certificates, infrastructure security, consulting) – highlight the role of cryptography in “Cryptographic Failures” (A04 2025).
- Offer supply-chain and dependency audits, especially for microservice, container, and SaaS-integrated systems.
The OWASP Top 10 2021 list remains a solid foundation (and should be treated as a minimum standard), but the 2025 edition stands out for extending its scope beyond code – encompassing the entire application ecosystem: artifacts, dependencies, operations, pipelines, exceptions, and logging/alerting. For IT teams, this means elevating the perspective – from “Is the code secure?” to “Is the entire process and runtime environment resilient and monitored?”